Serverless Authentication
I’ve created a simple PoC to test out Serverless Authentication for Lambdas using API Gateway Cognito Authorizer. It uses the Serverless Framework to configure/deploy, NodeJS for the Lambda.
The source and instructions are here.
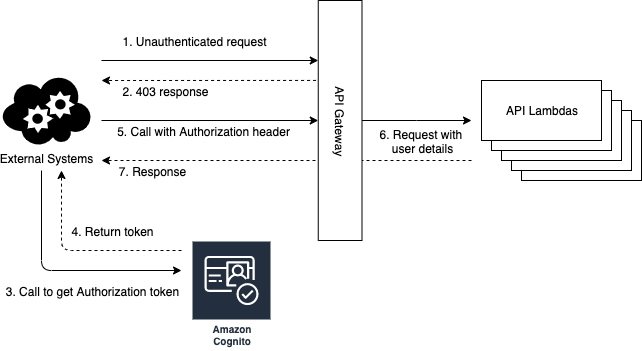
The advantage of this approach is that it is very quick and easy to setup, API Gateway manages authenticating requests and Cognito manages the users. You get the full set of Cognito functions for managing your users and only pay the cost for authentication calls and storage. The disadvantage is the authorization applies the whole API gateway and does not allow for role based access without customisation inside your Lambda code. You are also locked into Cognito, as it will be difficult to export user data and introduce a new authentication system.
This is a very nice way to quickly develop and expose API functions for external users, as you get a lot of scaling/security out of the box straight away without much work and custom code. If you look at the serverless.yml file the configuration is very simple.
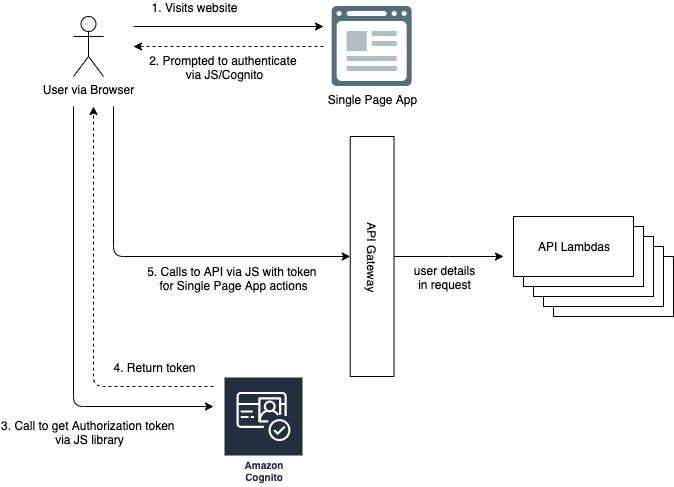
You can expand on this approach to create a web application, using a Single Page Application which prompts user to authenticate via Cognito and calls the API using the Authorization token for page actions to create a complex web application with authentication/persistence.
The main supported alternative for lambda authorization is using a Lambda as a custom authorizer, but this has other disadvantages, such as increased execution costs and performance, see here for details.